From Lure to Shell: Reproducing APT37’s CHM Exploitation Tactics
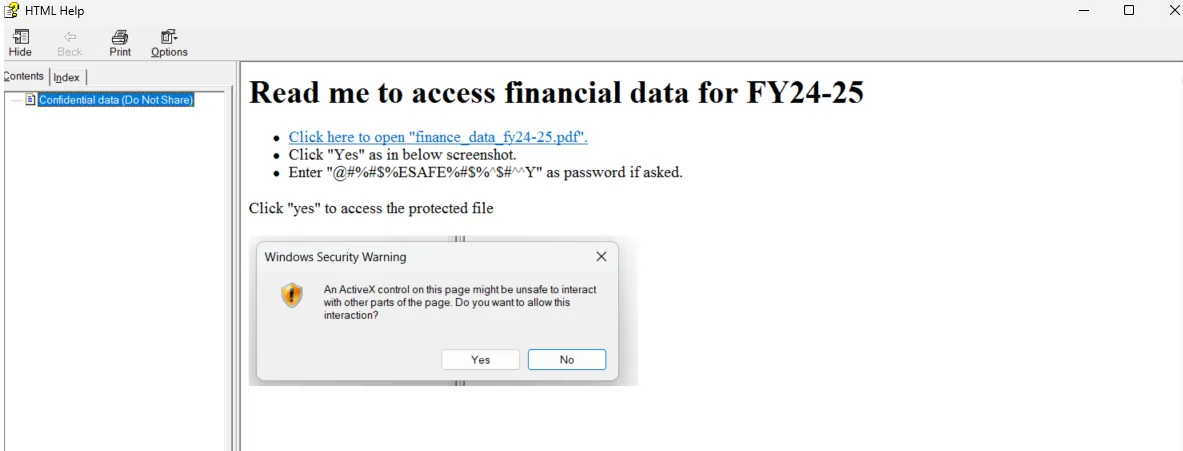
In this post, we explore how APT37 (Reaper), a North Korea-linked APT group, has weaponized CHM files in recent campaigns. More importantly, we demonstrate a red team simulation of this attack vector: using a CHM file that delivers a reverse shell under the guise of accessing financial data
Read Article